Cyber Security Course
Online Cyber Security course designed for everyone who has access to sensitive data, receives emails or uses the internet at work.
‘Cyber Security’ refers to a range of steps that protect sensitive information, systems, and networks from digital threats.
In November 2023 the UK’s head of the National Cyber Security Centre described the current threat level to digital infrastructure as ‘enduring and significant’.
However, with the right actions your staff can become a fortress against cyber threats.
This online Cyber Security training provides a general understanding to staff of how to defend against a range of common cyber attacks. Staff who handle personal data will also benefits from our Data Protection course.
Course Content
UNIT 1 – INTRODUCTION – In this first unit we explain what cyber security means and highlight common cyber threats and hacker techniques.
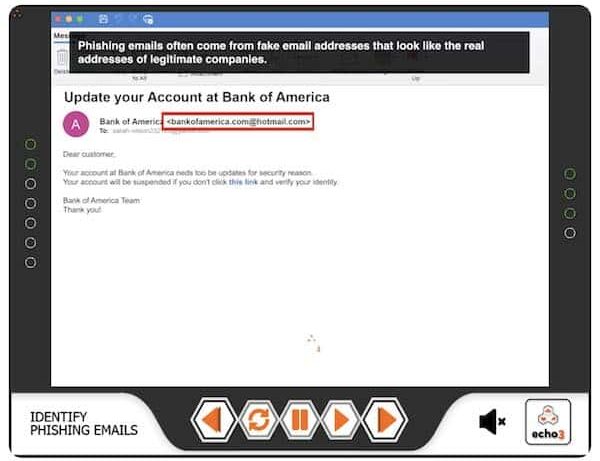
UNIT 2 – PHISHING – In unit 2 we cover phishing attacks in detail. So what they are, how to recognise them and importantly how to keep data safe.
UNIT 3 – MALWARE – In unit 3 explain what malware is, the common types and what to do if you suspect your computer has been infected.
UNIT 4 – SOCIAL ENGINEERING – In unit 4 we cover what social engineering is and how to protect yourself.
UNIT 5 – SECURITY – In this 5th unit we cover the simple best-practice steps you can take to keep the data you access safe. For example, using 2FA and keeping hardware safe.
UNIT 6 – MOBILE PHONES – In unit 6 we cover security threats related to smart phones and how to defend against them.
UNIT 7 – CLOUD SECURITY – In unit 7 we details the threats related to cloud computing and how to defend against them.
UNIT 8 – QUIZ – Achieve 80% or more and your CPD-accredited certificate will be email.
Cyber Security Course Certificate
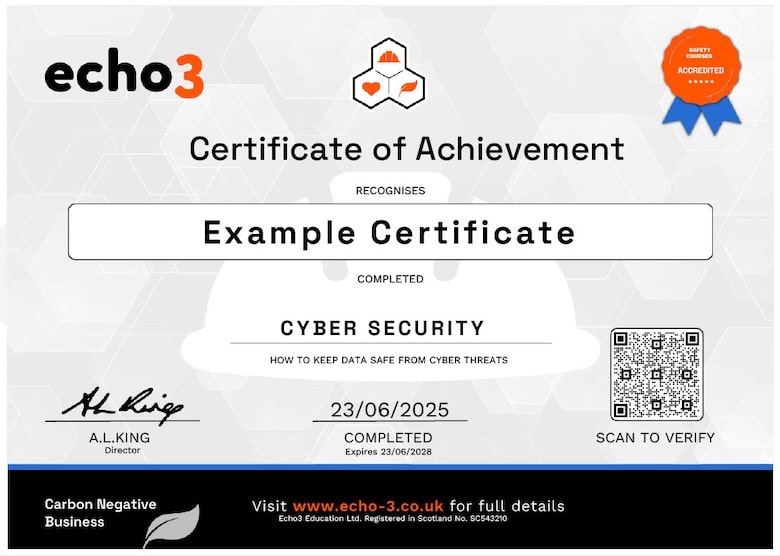
Download and Print Your Certificate
- Written in compliance with the UK GDPR and the Data Protection Act 2018
- Developed by qualified health and safety professionals Accredited by CPD – learn more about CPD here
- Last Updated June 2024
- To gain the certificate you must complete the assessment which involves 20 questions.
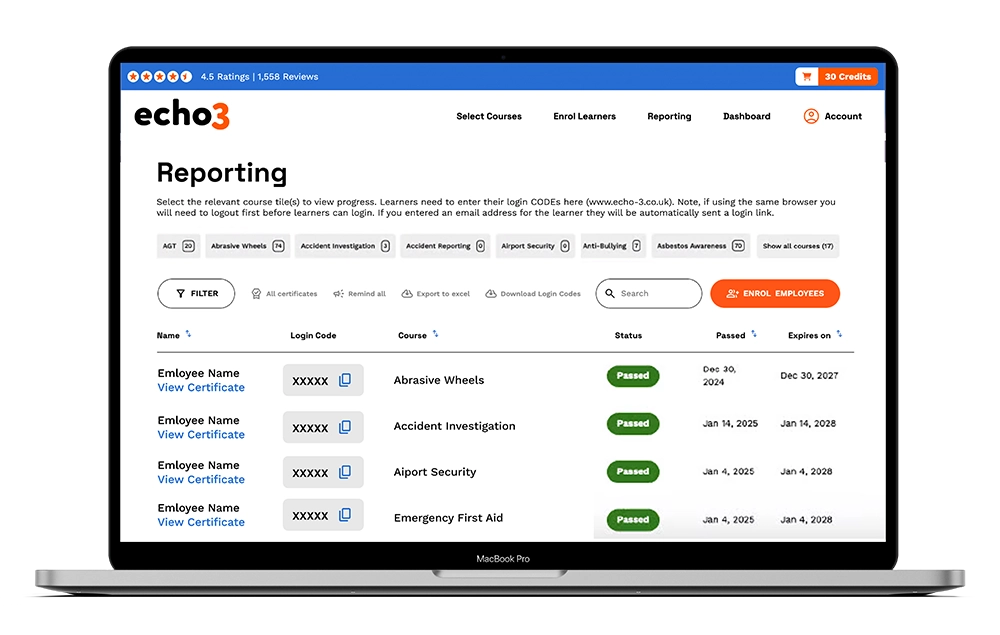
- You can access our LMS any time to reprint certificates, check and set pass marks and act as proof of a commitment to ongoing legal compliance.
- The online Cyber Security certificate is valid for 3 years.
Course Preview
Echo3 courses include engaging motion-graphic video content, with full english subtitles
Reviews
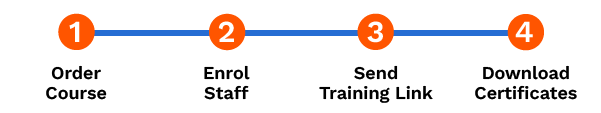
How to Get Certified in 3 Steps
Individual Learners

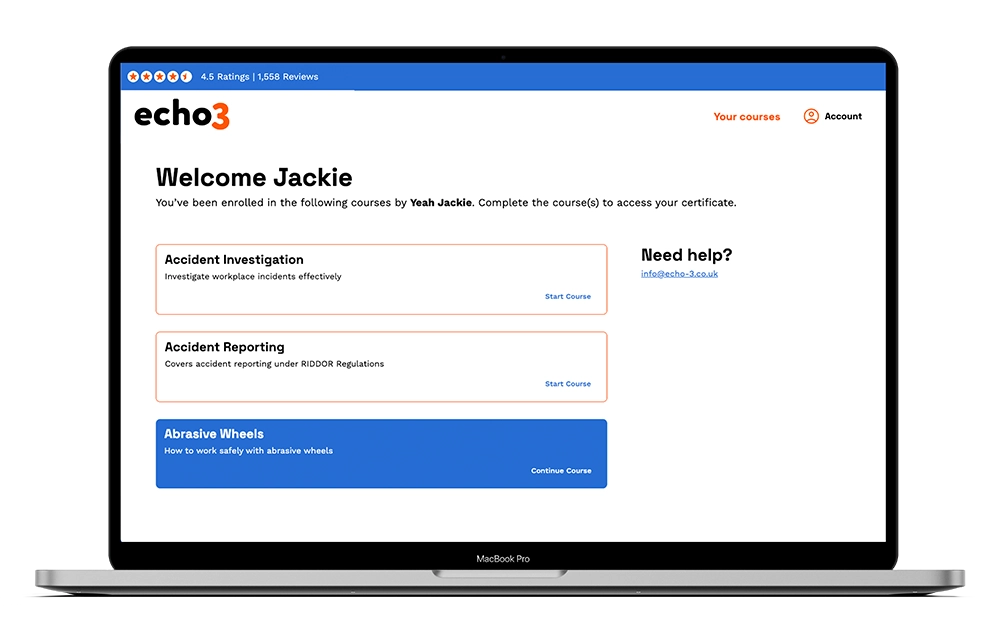
Benefits for Individuals
-
Engaging video-based content
-
Learner dashboard included
-
Instant access after payment
-
Free course retakes
-
Shareable digital certificate
 QR Code Certificate
QR Code Certificate




Bulk Buying Discounts
What is cyber security?
‘Cyber Threats’ are various malicious activities aimed at compromising computer systems or networks. Common types of attack are;
- Phishing,
- Malware,
- Ransomware,
- And hacking
‘Cyber Security‘ is the term used for the various countermeasures that together safeguard digital technologies from cyber threats thereby preventing unauthorised access, damage, financial and data loss.
Cyber security can be improved by non-technical staff with basic actions such as strong passwords, two-factor authentication and remaining vigilant against phishing attacks.
More technical cyber security measures include data encryption and firewalls can be implements by IT teams.
What are the learning outcomes of cyber security training?
The objectives of the Echo3 online Cyber Security course are to;
Raise Awareness of the Risk: Learners will appreciate the scale of the risks from cyber threats so they can access the time and attention to give the issue.
Recognise Threats: Hackers try to access our data in a variety of ways. You’ll learn their common techniques so you can spot attempts to access data.
Know How to Safeguard Data: This means preventing unauthorised access, theft, or manipulation of information.
Know How to respond to a Cyber Attack: If you suspect you’ve inadvertently downloaded malicious software you’ll learn how to respond.
Protect Infrastructure: Effective Cyber security can protect infrastructure. Because security breaches have the potential to disrupt the essential services within your business.
Maintain Trust: Cyber Security training help fosters trust among your clients that data flows will remain safe.
Prevent Financial Loss: Cyber-attacks can lead to significant financial losses. This Cyber Security course helps reduce this risk.
Who should take cyber security training?
 This cyber security course will benefit, anyone who uses digital devices, interacts with online systems, or handles sensitive data. To better protect themselves and their organisations from cyber threats. This includes.
This cyber security course will benefit, anyone who uses digital devices, interacts with online systems, or handles sensitive data. To better protect themselves and their organisations from cyber threats. This includes.
ADMINISTRATORS – All staff who have secure access to any of your internal software systems should understand how to keep passwords secure.
REMOTE COLLEAGUES – Anyone using company hardware for example laptops & mobiles are at greater risk. They should all know how to safely access wi-fi and protect hardware.
BUSINESS MANAGERS – Executives, managers, and business owners should understand cyber security basics to make informed decisions about protecting their company’s data and operations.
DATA HANDLERS – Everyone in your business with access to client, sensitive or personal data should know how keep this data safe for cyber threats. They will also benefit from GDPR Awareness, so data is processed correctly and now shared inappropriately.
What can staff do to help?
Staff can help secure your business from a cyber attack by implementing some simple but effective measures, for example;
- Using strong passwords and 2FA
- Keeping software up to date
- Utilising network security
- Encrypting sensitive data
- Keeping hardware like computers and phones safe
- And Vulnerability Assessments.
What are the different types of cyber attack?
Over 40% of businesses incur a successful cyber attack each year. The attacks take different forms including;
Malware. This is Malicious software designed to damage or disrupt computer systems, such as viruses, worms, and Trojan horses.
Phishing. These are by far the most common type of attack and take the form of deceptive emails or websites that trick users into revealing sensitive information, such as passwords or credit card details.
Ransomware. This is a form of Malware that encrypts a victim’s data and then demands payment for decryption.
Social Engineering. These are various manipulative techniques used to trick users into granting access or revealing confidential information.